In the realm of cybersecurity, WordPress hacking poses a persistent and concerning threat that necessitates immediate attention. Understanding the various types of WordPress hacking is crucial for mounting effective defense mechanisms. These include brute force attacks, cross-site scripting (XSS), SQL injections, and malware injections. Succumbing to such breaches can lead to severe repercussions. The compromised website may suffer from damaged integrity, loss of sensitive data, irreversible harm to the brand’s reputation, manipulation of search engine rankings, and the possibility of further cybercrimes.
Hacking Statistics in WordPress (source: https://www.getastra.com/blog/cms/hacking-statistics/)
- Due to its popularity, WordPress faces about 90,000 attacks per minute.
- Nearly 8% of WordPress websites are hacked due to weak passwords.
- WordPress websites are highly susceptible to vulnerabilities when they aren’t updated regularly.
- Nearly 61% of attacked websites were outdated.
- 52% of WordPress vulnerabilities arise from outdated plugins.
- Nearly 42% of WordPress sites have at least one vulnerable component to it.
- Compared to WordPress facing 95.6% of attacks, OpenCart only faces 0.35% of cyber attacks.
Common steps taken by hackers to hack the WordPress website
Identifying Vulnerabilities
Hackers locate vulnerabilities in your WordPress website, including accessing WordPress resources, monitoring security alerts, fostering a hacker community exchange, or knowledge sharing in the darknet.
Targeting and Attacking Victims
Hackers utilizing techniques like Google “Dorking” or relying on shared information within the hacker community and darknet to find any vulnerable WordPress sites base on the vulnerabilities information available. Google dorking, also known as Google hacking, is a technique that enables hackers to use advanced search queries to find specific information or vulnerabilities on websites. By refining search results, they can identify potential targets with weak security measures or installed vulnerable plugins.

Injecting Malicious Shell Scripts
Once the website has been targeted, in most case, hackers initiate their attacks by injecting malicious shell scripts.
What is Malicious Shell Scripts
Most of the malicious shell scripts invented are targeting on shared hosting web panel due to its virtual server environment’s security flaw, for instance cPanel, Directadmin, Plesk etc. These malicious shell script specifically crafted script that attackers inject into a compromised shared hosting web panel environment. The purpose of this script is to carry out further malicious activities, granting the hacker unauthorized access and control over the compromised system. These scripts often possess versatile functionalities, such as replicating themselves across different folders, executing SQL injections, injecting malicious scripts into web pages, accessing and manipulating files and directories, and even changing passwords.
Types of PHP Malicious Shell Scripts available in the public:
- shell-alfa
- shell-zehir4
- shell-efso
- shell-c99
- shell-wso
- shell-safe0ver
- shell-b374k
- shell-spynet
- shell-r57-bypass
- shell-webroot
- shell-symlink-v3
- shell-marijuana
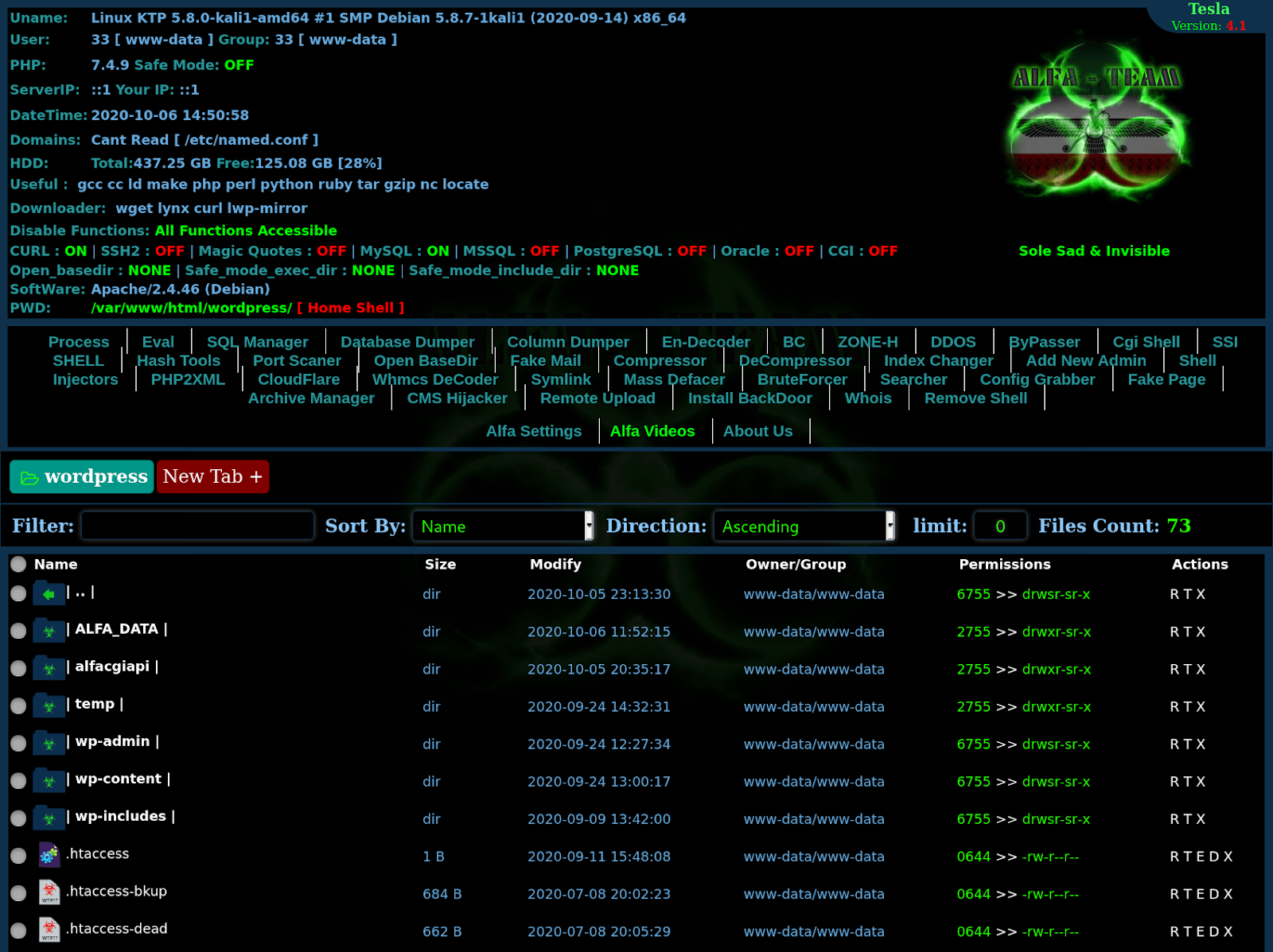
What kind of damages these malicious shell scripts will bring to your WordPress site
Once a potential target is chosen, hackers initiate their attacks by injecting malicious scripts. These nefarious shell scripts go unnoticed, allowing hackers to execute various actions. Shell scripts are a powerful tool utilized by hackers to achieve their objectives, and they can be classified into different categories based on their purpose and functionality.
The versatility of these malicious scripts is a cause for concern. Among their capabilities are duplicating themselves within multiple folders, conducting SQL injections, infiltrating scripts, unauthorized access to files and folders, alteration of passwords, site defacement, and SEO manipulations. These actions can have severe ramifications on a compromised WordPress website.
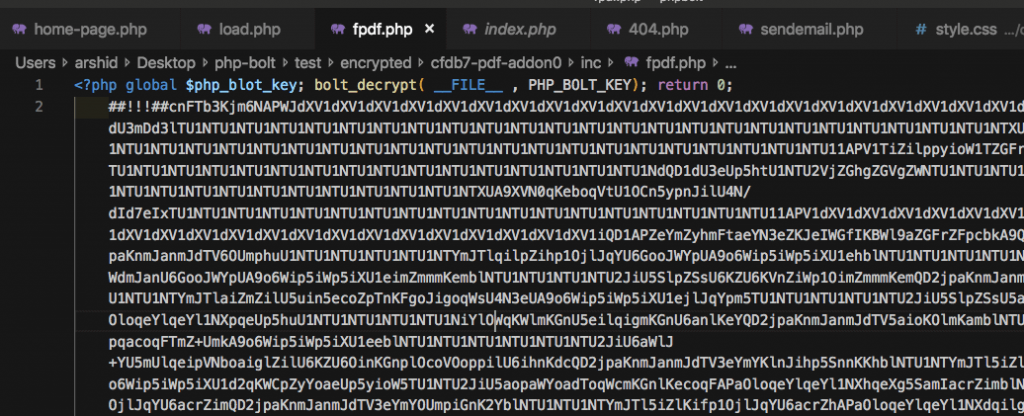
Why is it hard to trace and remove these malicious script?
Attempting to remove the malicious code can be an arduous task. Hackers often employ techniques such as obfuscation and encryption to camouflage their code, making it more challenging to detect and eliminate. Moreover, the spread of these malicious files across various locations within a website poses an additional hurdle to eradication efforts. In some cases, even when all traces of malware are erased, hackers persistently evolve and reinfect compromised websites, necessitating ongoing vigilance.
How do you reduce the likelihood of your WordPress being hacked
The responsibility for safeguarding your website falls squarely on your shoulders. To minimize the likelihood of falling victim to WordPress hacking, there are several steps you can take. First and foremost, refrain from using untrusted or nulled templates and plugins, as they can introduce vulnerabilities into your website. Regularly updating your WordPress core, themes, and plugins is crucial, as these updates often address security loopholes. Establishing a routine backup process will ensure you can easily restore your website’s data in the event of a security breach.
Additionally, implementing reputable security plugins is strongly recommended. These plugins help fortify your website’s defenses and mitigate potential threats. Configure them judiciously to gain maximum protection. In the unfortunate event of a security breach, it is vital to promptly report the incident to your hosting provider. They can provide valuable assistance in investigating and uncovering any vulnerabilities present.
In conclusion
WordPress hacking continues to be a sobering threat. To protect your WordPress website, it is imperative that users understand the steps employed by hackers and implement strategies to safeguard against them. Stay vigilant, prioritize security measures, and remain in control of your online presence. By adopting a proactive approach, you can build a robust defense to safeguard your WordPress website from these persistent cyber threats.
DISCLAIMER: This article aims to educate WordPress users about the tactics employed by hackers. No malicious intent should be derived from these explanations.