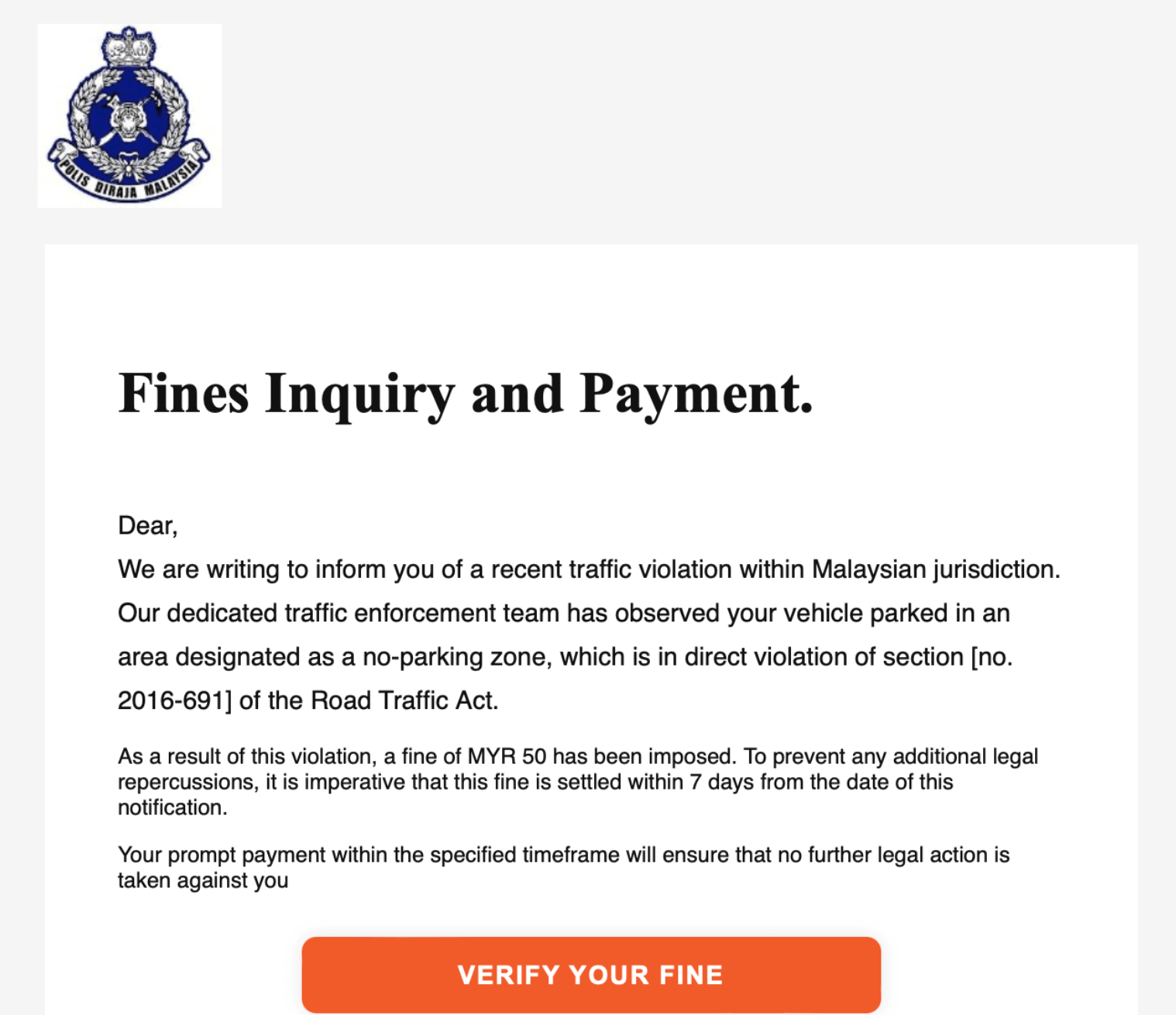
As a web security expert specializing in combating phishing websites, I am committed to keeping my readers informed about the latest threats and providing them with the necessary knowledge to stay protected. In my recent investigations, I have discovered a new kind of phishing website that specifically targets users in Malaysia. These sophisticated phishing sites dynamically alter their content based on the visitor’s IP address. If the IP is detected as a Malaysian IP, the site displays phishing content, but for others, it appears as a harmless 404 page. This clever tactic allows these malicious actors to evade detection by anti-phishing reporting sites.
In this article, I will not only shed light on this emerging threat but also educate readers on how to identify phishing websites, report them to the relevant authorities in Malaysia, and utilize helpful tools such as the PhishDetector Chrome extension to identify potential risks. It is crucial for readers to remain calm and vigilant when encountering suspicious emails or ads, always conducting fact-checks and refraining from sharing sensitive information such as passwords or financial credentials with suspicious websites.
Understanding Phishing Websites
Phishing websites have become increasingly sophisticated, making it challenging for users to differentiate between legitimate sites and fraudulent ones. These websites are designed to deceive users into revealing sensitive information such as login credentials, credit card details, or personal data. Phishing attacks can occur through various channels, including emails, social media messages, or even ads on trusted websites.
Identifying Phishing Websites
Recognizing the signs of a phishing website is essential to protect yourself online. Here are some key indicators to watch out for:
1. Suspicious URLs
Phishing websites often use deceptive URLs that resemble legitimate ones. Carefully examine the URL for any misspellings, added numbers, or unfamiliar domain extensions. For instance, a phishing site may use “www.yourbank-login.com” instead of the legitimate “www.yourbank.com“.

2. Urgency and Fear Tactics
Phishing attacks often rely on creating a sense of urgency or fear to manipulate users into taking immediate action. These tactics include threatening consequences if you do not provide personal information quickly. Remember, legitimate organizations will never ask for sensitive information via email or other insecure channels.
3. Suspicious Requests for Personal Information
Phishing websites frequently ask users to provide personal or financial information that legitimate organizations would not typically request via email or unsolicited messages. Exercise caution when asked to provide sensitive data, such as passwords, Social Security numbers, or credit card details. 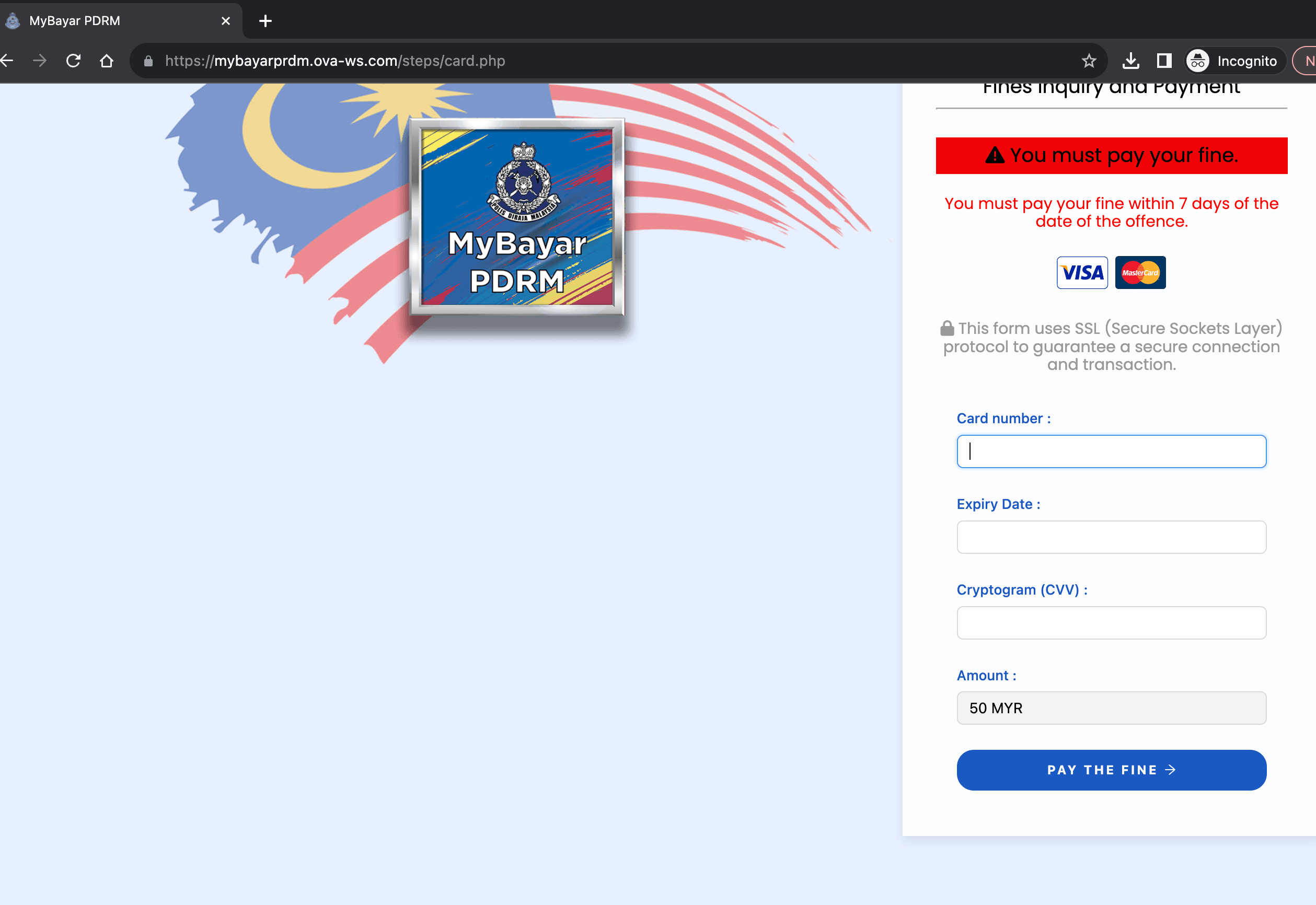
Common Ways Scammers Distribute Phishing Websites or Mobile Applications Installer
1. Email Phishing
Email remains a popular medium for scammers to distribute phishing URLs and malicious mobile applications. They send deceptive emails posing as trusted organizations, urging recipients to click on a link or download an attachment that leads to a phishing site or malicious app. Exercise caution when receiving emails from unknown senders or those that seem suspicious, especially if they request personal information or prompt you to download files.
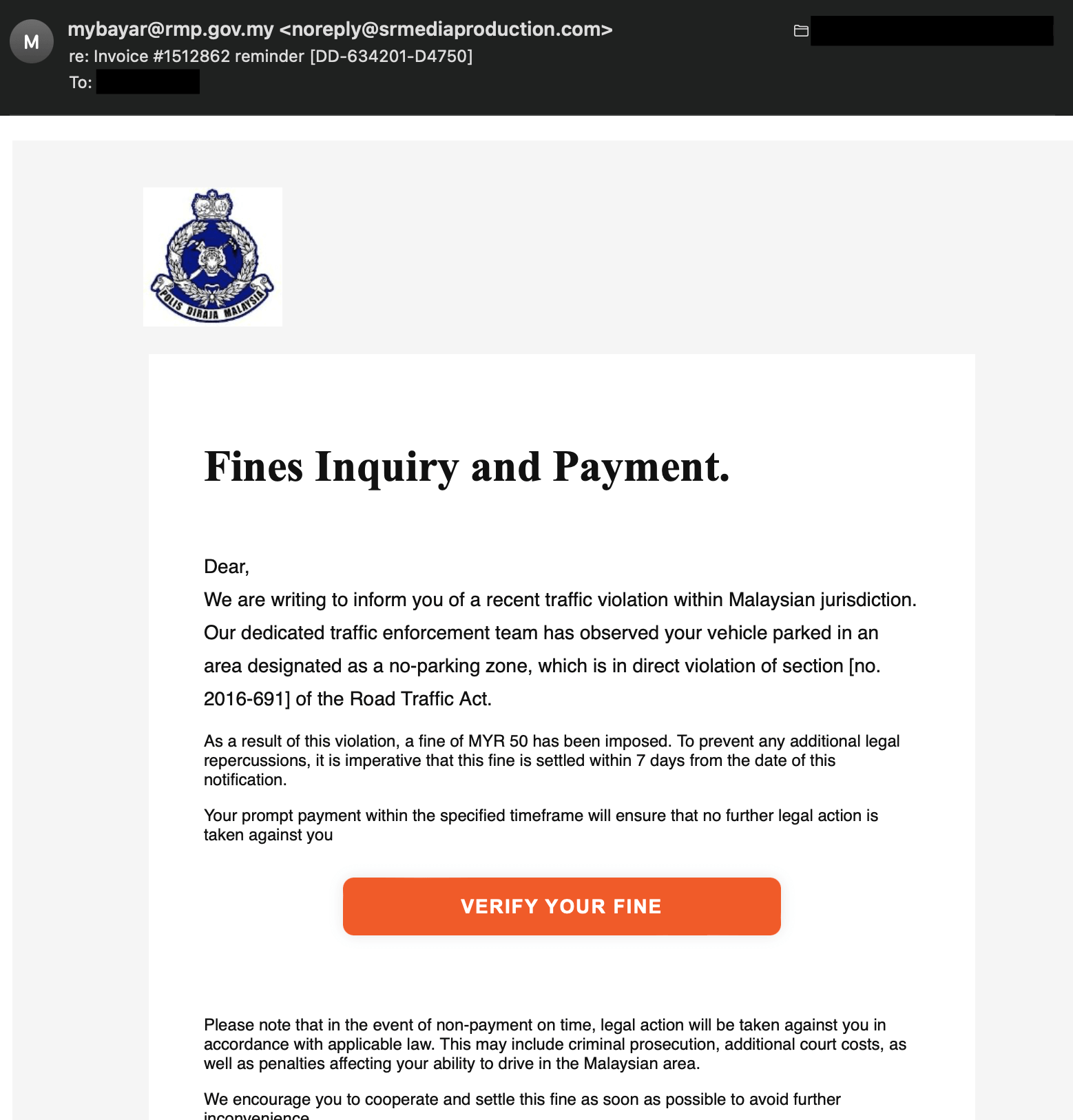
2. Social Media
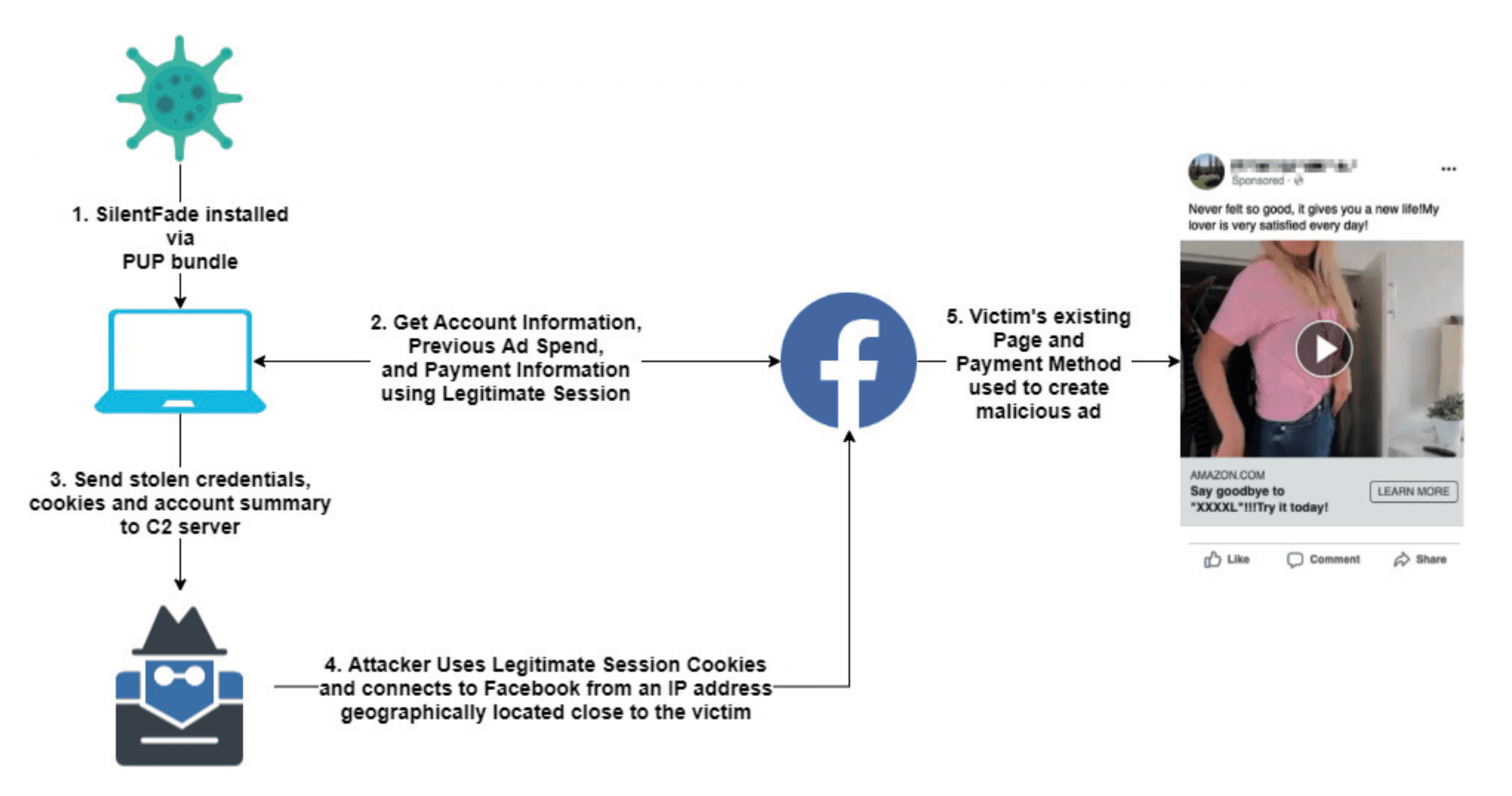
Social media platforms have become a breeding ground for phishing scams. Scammers leverage social media ads, messages, and posts to distribute phishing URLs and promote malicious mobile applications. These ads or messages often entice users with alluring offers or urgent notifications, encouraging them to click on a link or download an app that leads to a phishing site or infects their device. Be cautious when interacting with unknown individuals, suspicious ads, or messages that redirect you to unfamiliar websites or app stores.
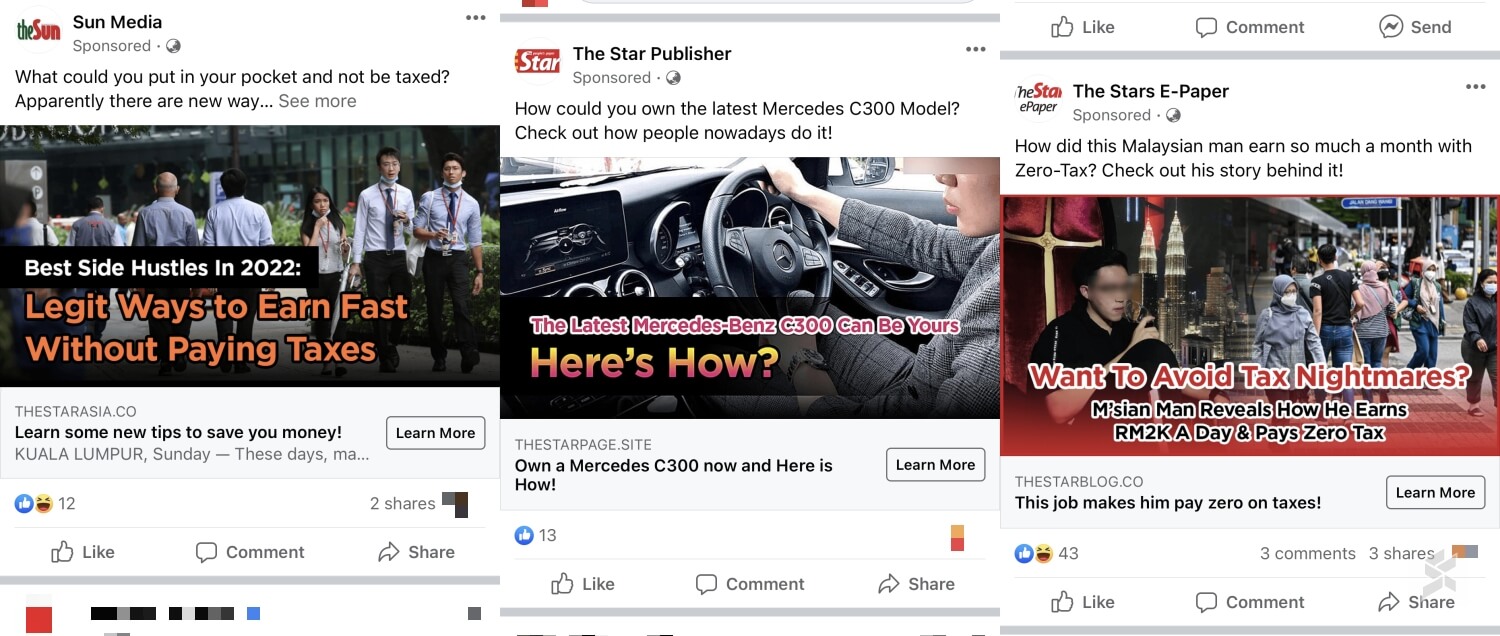
3. Malvertising
Malvertising, short for malicious advertising, involves scammers injecting malicious code into legitimate advertisements displayed on trusted websites. Clicking on these ads may lead to phishing sites or prompt the download of malicious mobile applications. Even reputable websites can unknowingly display these ads, making it challenging to identify potential threats. To mitigate risks, exercise caution when clicking on ads and consider using ad-blockers or browser extensions that help detect and block malicious advertisements.
4. Search Engine Manipulation
Phishing scammers manipulate search engine results to promote their phishing URLs and malicious mobile applications. By using search engine optimization techniques, they increase the visibility of their fraudulent content. When users search for specific keywords, these manipulated results may appear among the top search results, leading them to phishing sites or malicious app downloads. Always verify the authenticity of the websites or app stores before clicking on any links or downloading applications.
5. Third-Party App Stores
Scammers often target users who download applications from third-party app stores rather than official sources such as Google Play Store or Apple App Store. These malicious applications may mimic popular apps or offer enticing features, but once installed, they can compromise the security of the user’s device and personal information. To minimize risks, only download applications from trusted sources and enable the necessary security settings on your device to prevent the installation of apps from unknown sources.
Reporting Phishing Websites & Mobile Apps in Malaysia
When you encounter a phishing website targeting Malaysia, it is crucial to report it to the relevant authorities. By reporting these sites, you contribute to the fight against cybercrime and protect others from falling victim to these scams. Here’s how you can report a phishing website in Malaysia:
1. MyCERT (Computer Emergency Response Team)
MyCERT is the designated agency in Malaysia for handling cybersecurity incidents. If you come across a phishing website, you can report it to MyCERT by visiting their website (https://www.mycert.org.my) and providing detailed information about the suspicious site. MyCERT will investigate and take appropriate action to mitigate the threat.
2. Malaysian Communications and Multimedia Commission (MCMC)
The MCMC is responsible for regulating and monitoring communications and multimedia services in Malaysia. To report a phishing website, you can contact the MCMC through their website (https://www.mcmc.gov.my) or call their hotline. Provide them with relevant details, including the website URL, screenshots, and any additional information that may assist in their investigation.
Utilizing Tools for Phishing Detection
To bolster your protection against phishing attacks, consider leveraging tools designed to detect and alert you to potential threats. Personally, I will be using Suspicious Site Reporter by Google & PhishDetector – True Phishing Detection Chrome extension to make sure the website I’m visiting isn’t a phishing or suspicious site. These powerful browser extensions analyze websites for potential phishing indicators and alert you if it detect any suspicious elements. By installing these extension, you can add an extra layer of security to your browsing experience.
Conclusion
As the threat landscape continues to evolve, it is crucial to stay informed and educated about the latest phishing attacks. By familiarizing yourself with the signs of a phishing website, reporting suspicious sites to the appropriate authorities, and utilizing tools like PhishDetector, you can significantly reduce the risk of falling victim to these scams. Remember, always exercise caution, conduct fact-checks, and never share sensitive information with suspicious websites. Stay safe and protect yourself online!